TL;DR
The CLOUD Act gives U.S. authorities the legal right to access data held by U.S. cloud providers regardless of where the data is stored. For governments and critical industries, this creates a direct sovereignty risk: foreign warrants can reach into national infrastructure, healthcare systems, financial networks, and even defense operations.
To maintain control, nations must rebuild Jurisdictional Immunity, a digital architecture that ensures sensitive data, models, and infrastructure remain under local law only.
In 2013, a drug trafficking case in New York sparked a legal battle that would redefine data sovereignty for a generation. The U.S. government served Microsoft with a warrant for a suspect’s emails. Microsoft complied, but with a catch: the data was stored on a server in Dublin, Ireland.
Microsoft refused to hand over the Irish data, arguing a U.S. warrant couldn’t reach across the Atlantic. The U.S. government argued that because Microsoft was a U.S. company, it controlled the data no matter where it was physically stored. The case, United States v. Microsoft, went all the way to the Supreme Court, creating immense uncertainty for the entire cloud industry.
In 2018, the U.S. Congress ended the debate not with a court ruling, but with a new law: the CLOUD Act. It effectively sided with the government’s position, cementing a principle that keeps government and industry leaders awake at night: in the digital world, your data can be subject to another nation’s laws, even when stored on your own soil.
For governments and industries like finance, healthcare, and energy, this isn’t a theoretical legal debate. The cloud is the backbone of modern operations, and this dependency creates a hidden vulnerability. Understanding the CLOUD Act isn’t a legal exercise; it’s a fundamental requirement for national security and sovereign AI compliance.
Let’s break down this complex act, its direct implications, and the strategic path forward.
The CLOUD Act, Simplified: A Two-Way Street for Data
The CLOUD Act has two core pillars:
Extraterritorial Reach
U.S. authorities can compel U.S. cloud companies to produce data stored anywhere in the world.Bilateral Data-Sharing Agreements
The U.S. can establish “executive agreements,” allowing partner governments to directly request data from U.S. companies without going through MLATs (Mutual Legal Assistance Treaty).
While meant to streamline cross-border investigations, the law introduces profound sovereignty risks for non-U.S. jurisdictions.
The New Digital Power Struggle
The CLOUD Act marks a turning point in global digital governance. It reinforces a geopolitical reality:
Physical location no longer defines legal control, corporate nationality does.
This opens the door for other major powers to create their own equivalents. Imagine a scenario where:
The U.S. demands data stored in Beijing.
China issues its own legal demand for the same dataset.
The cloud provider faces impossible, conflicting obligations.
This is the accelerating “Splinternet”, the fragmentation of legal authority over digital assets.
For nations, the implications are clear:
- Critical infrastructure could fall under foreign jurisdiction.
AI models trained on national datasets become indirectly exposed.
Competitive industries lose control over their intellectual capital.
This is no longer about privacy; it is about state sovereignty.
The Missing Shield: Reclaiming "Jurisdictional Immunity"
In the physical world, sovereignty is simple: a building in Berlin follows German law. A military base in France answers to France alone.
Digitally, this protection has weakened.
Jurisdictional Immunity is the principle that a nation’s digital assets, data, models, and infrastructure, must fall exclusively under local law.
The CLOUD Act breaks that shield:
if your critical systems rely on a U.S. cloud provider, they fall under U.S. legal jurisdiction, regardless of where the servers sit.
Rebuilding this protection is the foundation of digital sovereignty.
The Chain of Risk: The High Cost of a Missing Shield
Without jurisdictional immunity, nations face a predictable cascade of consequences:
No Immunity → No Guarantee of Data Control → CLOUD Act Exposure → Economic & Strategic Vulnerability

The impact includes:
Economic disadvantage: sensitive industries relocate to jurisdictions with stronger sovereignty.
Forced technological alignment: national digital futures become tied to foreign legal systems.
Institutional distrust: citizens and businesses lose confidence in national protection.
These risks materialize across every critical sector.
Implications for Critical Industries
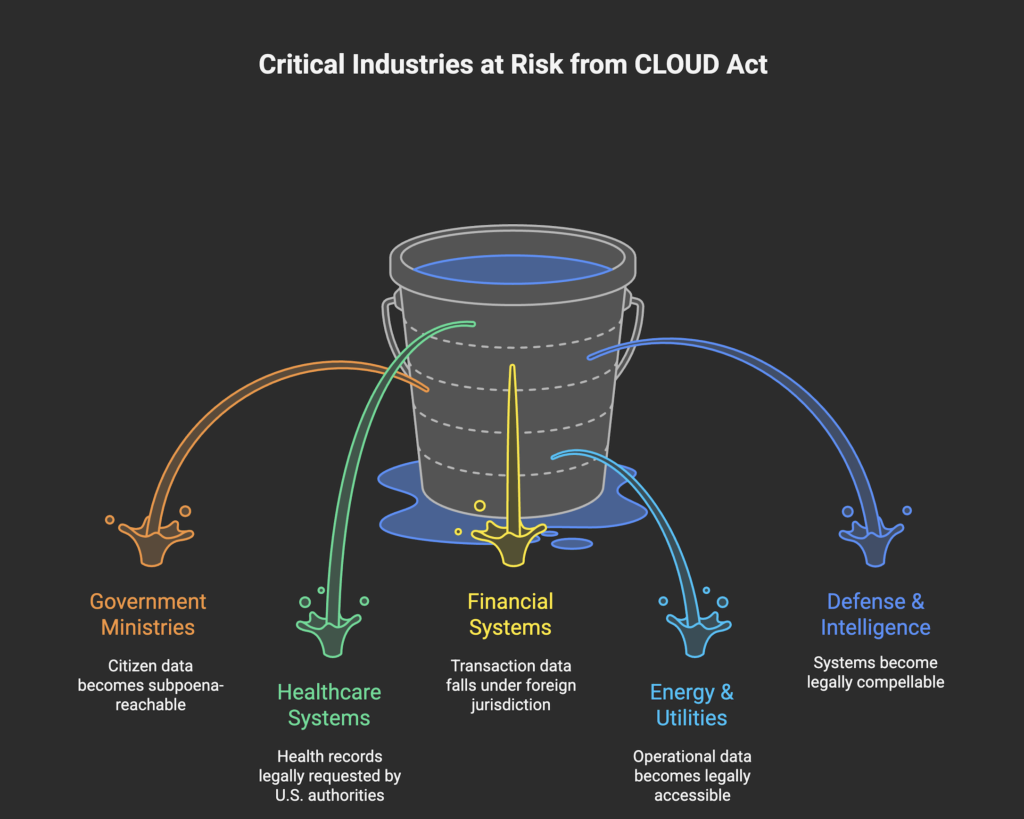
Government Ministries
Government systems contain:
citizen data, law enforcement records, intelligence insights, tax files, border data.
With U.S. cloud providers:
Confidential data becomes subpoena-reachable.
Critical workflows can be interrupted by foreign legal action.
AI models trained on national datasets lose sovereign protection.
This is fundamentally a sovereignty issue, not a compliance checkbox.
Healthcare
Healthcare systems manage the most sensitive national datasets: genomics, patient histories, epidemiological models.
Under the CLOUD Act:
Health records stored on U.S. clouds can be legally requested by U.S. authorities.
Local medical privacy laws are overridden.
Public-health AI models become indirectly exposed.
This is a direct breach of national medical confidentiality and bio-security.
Financial Systems & Central Banks
Financial systems rely heavily on cloud-based infrastructure.
CLOUD Act exposure means:
Transaction data and banking metadata fall under foreign jurisdiction.
Central banks risk losing regulatory exclusivity.
Market confidence weakens when jurisdictional control is uncertain.
This creates instability incompatible with financial sovereignty.
Energy, Utilities & Critical Infrastructure
Modern infrastructure runs on cloud-based telemetry and AI optimization.
If hosted on U.S. clouds:
Operational data becomes legally accessible.
Vulnerabilities in grids, water systems, or telecoms may be indirectly exposed.
Geopolitical tension can turn into cyber or legal leverage.
Infrastructure under foreign jurisdiction is a national risk.
Defense & Intelligence
For defense organizations, CLOUD Act exposure is a hard stop.
Systems such as surveillance, logistics, battlefield models, or classified analytics must never be under foreign jurisdiction.
If they touch U.S. cloud infrastructure:
They become legally compellable.
Encryption alone is not enough unless key management is sovereign.
Allies may reduce cooperation.
For national security, this risk is unacceptable.
The Strategic Imperative: Rebuilding Jurisdictional Immunity
Achieving jurisdictional immunity is not an IT initiative, it is a national security mandate. Nations must rebuild a digital core that is legally untouchable, architected so that their most sensitive systems, models, and datasets fall exclusively under local law. This doesn’t mean abandoning global cloud entirely; it means drawing a firm boundary between what must remain sovereign and what can remain global. Without this shield, governments and critical industries will continue operating in a world where foreign jurisdictions can reach directly into their most vital digital assets.
Conclusion
The Microsoft Ireland case signaled an early warning, and the CLOUD Act clarified the stakes. We now understand the long-term implications.
For today’s leaders, the focus is no longer on whether to pursue sovereign digital infrastructure, but on how to implement it effectively. Jurisdictional immunity is becoming a key principle of modern digital governance.
Nations that take practical steps toward strengthening their sovereign foundations will be better prepared for the future.




